What Is an Antipersona?
Imagine a safe-manufacturing company. Such a company would need to design safes that:
- are easy to use and satisfy the needs of its target customers, and
- are hard to break into by burglars.
To address the first of these two requirements, the company has to research its target customers and understand their needs. But to address the second, it must study the burglars’ behaviors, methods, and tools — even though burglars are not among the company’s target audience.
Definition: An antipersona is a representation of a user group that could misuse a product in ways that negatively impact target users and the business.
Product misuse may threaten regular users' safety, security, confidence, loyalty, and retention. Antipersonas can help reduce these risks. For example, in 2012, Procter and Gamble released Tide Pods to the public. The colorful detergent pods were so appealing that they looked edible to an audience of adolescents on social media, who consumed them as part of a social-media challenge. The effect of this misuse was catastrophic –- not only did it damage trust in the brand, but it also endangered the health of those who ate the pods. In the aftermath, Procter and Gamble invested in child-proof repackaging and product-marketing recovery. If the product team had investigated this possible misuse as part of antipersona creation, it may have been able to implement safeguards before the initial launch.
When Does It Make Sense to Create an Antipersona?
Not all misuse of a product is equally dangerous, risky, or complex to warrant the creation of an antipersona. The process of creating an antipersona does require time and resources, and thus, it is worth it only if the benefits outweigh the costs.
For example, a luxury-hotel might get occasional calls from people who cannot afford a stay there. It would not be necessary to create an antipersona for these users since the cost of dealing with these calls will likely be a lot smaller than creating an antipersona and using it to find solutions that prevent these calls.
Usually, creating an antipersona makes sense if your product or service:
- deals with sensitive information that, if inadvertently exposed, can threaten the users’ or organization wellbeing (e.g., fraud, identity theft, harassment, disinformation, illegal content)
- poses potential physical or emotional threats to people (e.g., injury, or death as the direct result of misusing the product).
If there is an opportunity for these harms to occur as the direct result of anyone using the product, there should be one or more antipersonas to represent the risk. Always balance the chance of such a misuse with its consequences in order to determine if an antipersona is worth creating. Even a misuse that is very unlikely to happen might be worth of an antipersona if its consequences are extreme.
What Information Should Be Included in an Antipersona?
Like personas, antipersonas are a schematic representation of a group of people. Unlike personas, which are used to build empathy with target users, antipersonas are meant to give product-design teams and businesses awareness of major risks that they should strive to mitigate and also potential clues about how to mitigate them.
An antipersona should contain:
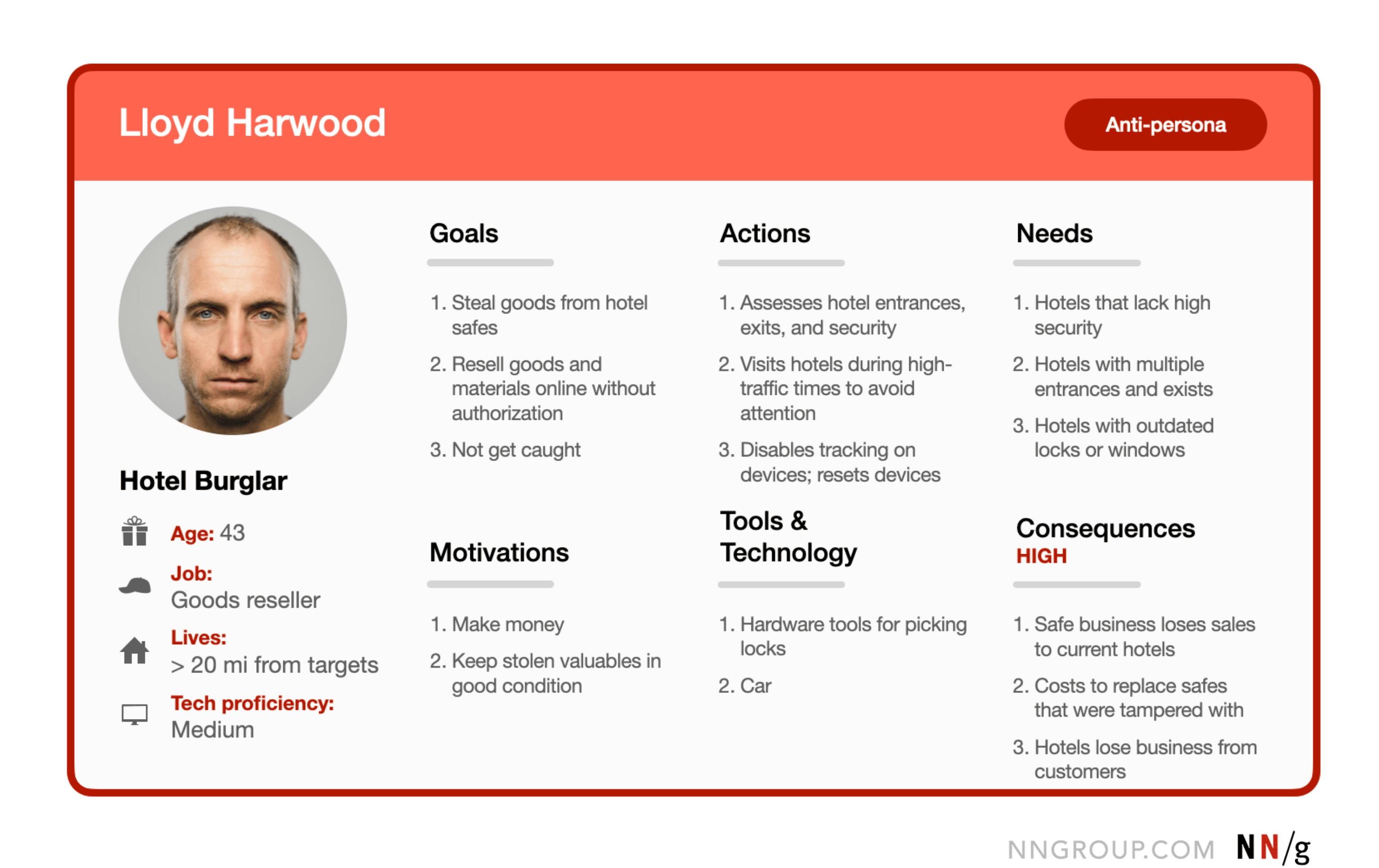
Name and face
Including a name and face helps to frame the antipersona as a real threat and increase its memorability.
Goal
The goal is the most important component of the antipersona and should be a description of the threat rather than an explanation of why the threat occurs. In the example of safes, the burglar is an antipersona and their goal is to steal valuables from the safe.
Motivations
Motivations should reveal the root cause behind why the antipersona wants to accomplish this goal. Motivations are different from goals. For example, a burglar might have the goal of covertly stealing valuables from hotel safes, but their motivation is to make grand sums of money by reselling the stolen items online. Motivations help us to understand the actions that the antipersona will take to achieve their goal of misusing the product. In our example, if burglars are motivated to resell the stolen items, they will want them in good condition, so they might not take a hammer to the safe. It’s more likely that they would, instead, try to circumvent the lock.
Actions
This antipersona component should explicitly detail the actions that the antipersona takes in order to achieve their goals. Action-related information can call attention to infrastructure that enables the antipersona’s actions. For example, burglars will need to plan an entrance and exit strategy in the hotel; that action will depend on how easily they can acquire a detailed map of hotel grounds with entrances and exits.
Tools
Tools should outline the technologies that the antipersona can use to accomplish their goal. If the burglar might covertly crack the safe lock using a tool like a paperclip, then the lock design and technology will matter more than the safe-box material.
Needs
To assess needs, product designers might ask themselves: What does the antipersona need to be in place to achieve their goal(s)? These factors will usually be extremely contextual. In our safe example, burglars might need hotels without security guards or without extensive surveillance technology. The hotels might also need to have multiple entrances open to the public and cars. These needs are very specific to successfully executing the antipersona behaviors.
Consequences
How would the target users and the business be affected if the antipersona achieved their goal? If a burglar were able to covertly steal valuables out of a safe, target users would lose their valuables and their trust in hotel safes. Hotels might lose customers when it becomes known that their safes are vulnerable to burglary and may no longer purchase safes where they once did, which would mean that the safe business would lose revenue. Additionally, the business may increase prices for the most secure safes and choose to market to hotels with higher security at a lower cost.
Who Is Responsible for Creating Antipersonas?
User researchers and product designers leverage insights from discovery work and persona-related research to lead the creation of antipersonas. They should involve product partners and stakeholders throughout the process of creating antipersonas, to increase the likelihood of adoption.
Method for Creating Antipersonas: Identify Threats
An easy way to create antipersona is to start with the highest-consequence, critical threats first. This approach works especially well if the creation of antipersonas is new to the team. Your team should adapt these threats to your product context, but these are a few common threats to use as a starting point:
1. The thief
There are two common types of theft to anticipate:
- Information theft, which involves any product dealing with sensitive information, where there are actors who would like to acquire that information without permission
- Physical theft, which involves any product that could physically be stolen
2. The creator or sharer of illegal content
If your product enables people to communicate freely, it is possible for all types of illegal content to arise, including hate speech, child sexual-abuse material (CSAM), and content that shows or promotes extreme violence. Not only are these forms of content illegal, but they can severely damage the target user’s experience.
3. The creator or sharer of disinformation
If your product enables people to communicate and share content freely, it is possible for disinformation to spread. Disinformation can negatively impact users’ perception of your brand and trust in it.
4. The child
Ask yourself if misuse of your product could harm a child either physically (think about pill bottles or knives) or emotionally (e.g., sexually explicit, violent content).
Flesh out these common antipersonas by asking the following questions:
- What is the goal of the antipersona? What will achieving that goal further enable them to do (e.g., piracy, ransomware in the case of information theft)?
- What are the potential motivations behind this goal?
- What are the tools that the antipersona can use to achieve this goal –- whether software, skills, or training?
- What needs to be in place for this goal to happen? In other words, what protections are not in place that might enable the antipersona?
- What are the consequences of the antipersona achieving their goal?
Validate through Research
When possible, teams should conduct discovery research with people that are similar to their antipersonas, because the true likelihood of misuse and its consequences will likely not be completely uncovered without real research. Some antipersonas (e.g., children) may be easy to get in the lab and research, while others may involve sleuth work and using a variety of existing literature and resources.
Even though you may not have access to the people represented by your antipersonas, you may be able to reach experts in those behaviors (for example, lawyers or social workers who may be involved with incarcerated people committing comparable crimes) or people similar to them. For example, it would be difficult to interview a real hacker who is maliciously trying to break into a website, but it would be possible to interview a professional hacker that gets paid to find vulnerabilities in websites. Or, in the burglar example, one may reach out to hotel personnel and security guards, who could provide their observations.
Conclusion
Antipersonas help businesses to anticipate and mitigate risks associated with the misuse of their products. If you are considering an antipersona associated with a possible type misuse, weigh how likely that misuse is with its consequences. Even low-probability misuse may need to be prevented and represented by an antipersona if the consequences are major.




